Unify the management of your devices
Optimize the performance of your IT assets and increase the productivity of your employees.

- Do you ensure that your IT resources (laptops, desktops, mobile devices, software applications, and business data) are used effectively both inside and outside the office?
- Do you have full, secure remote access to the equipment used by your employees for real-time monitoring or assistance from anywhere in the world?
- Can you ensure that your company's corporate data is protected and that you have a simple, secure, and efficient way to recover it, preventing its loss?
- Do you have complete control over your company's mobile devices, under a centralized access management model where you can define application usage, data consumption, and information security?

Know the real status of your IT resources
Performs automatic hardware and software inventories, detects licensed and unlicensed software installed on each device, license costs, and information related to programs and operating systems.
Detects installed licenses for each device and controls software licensing for your computers.
Learn about the software resources acquired by your organization, their value and location, facilitating the management of purchasing, use, control, and updating of these assets.
Keep all workstations in your organization up to date without interrupting your employees' work.
Prevent external attacks and security risks by keeping all workstations in your organization up to date with the latest patches and updates released by solution manufacturers.
Centrally distribute software and file installations across your corporate network
Schedule the automatic distribution and installation of the software and files required by your remote team, unattended and without interfering with your employees' productivity.
Mobile device inventory and application management
Get to know the real status of your mobile device network with up-to-date details on device hardware, installed applications, status, location, network characteristics, manufacturers, operating systems, and location, which can be viewed from the administration console at any time.
Management and enforcement of behavior policies on your devices
The IT administrator can send the initial configuration required for the devices to be used properly to the mobile phones: access to Wi-Fi networks, employee email, applications necessary for work, restrictions to ensure proper use of the device, lists of required/prohibited applications, password policies, etc.
Business rule sets + Voice and data
Sets of business rules can be assigned to devices to define their behavior in response to relevant events, such as entering or leaving geographic zones (geofencing), mobile device unlinking initiated from the device, unlinking performed from the console, policy violations, jailbreak detection, rooting detection, among others.
Secure separation of corporate and personal environments
Securely manage corporate applications and information shared on devices that use separate environments (Android for Work) within your organization, while keeping the personal data and content of device owners protected.
Backup and Recovery
Offer your organization powerful multi-layered protection against data theft and unauthorized access to your backed-up files through features such as endpoint encryption, remote wipe, and data theft prevention.
Reduces the risk of data migration
The IT department can easily locate and back up critical data stored in undefined locations on desktops or laptops, reducing the risk of failing to migrate all critical business information.
Data protection on mobile devices
Encryption of corporate data stored on the device, remote wipe, secure lockdown, and real-time geolocation, while providing reliable access to organizational documents with different levels of access control.
Backup of Microsoft email PST files
Support for open files through integration with Microsoft VSS allows you to back up PST files while Microsoft Outlook is open.
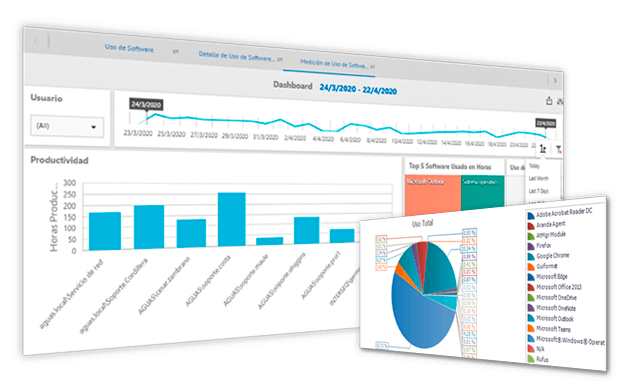
Define productivity indicators based on application usage
Identify the usage levels of the tools installed on each workstation over a given period of time (days, weeks, months, or critical periods).
Remote control and management
Performs monitoring and administration activities on each workstation, carrying out all configuration tasks remotely, such as shutting down or restarting the workstation, deleting a file, among others.
Monitor unauthorized actions performed by remote users on devices
Detects actions such as software installations, hardware tampering, service shutdowns, creation of shared resources, installation of virtual VPN adapters, and unauthorized user access to computers, among others.
Analyze the performance of your employees
Access historical reports or logs of all software usage by setting up measurements by category: date, period, user, file, license, or application, regardless of the brand and/or software manufacturer.
