Unifica la gestión de tus dispositivos
Optimiza el desempeño de los activos de TI e incrementa la productividad de tus colaboradores.

- ¿Controlas que tus recursos informáticos (Laptops, equipos de escritorio, dispositivos móviles, aplicaciones de software y data empresarial) se utilicen de manera efectiva dentro y fuera de la oficina?
- ¿Tienes acceso remoto total y seguro a los equipos que utilizan tus colaboradores en caso de monitoreo o asistencia en tiempo real desde cualquier parte del mundo?
- ¿Puedes asegurar que los datos corporativos de tu compañía están protegidos y tienes una forma simple, segura y eficiente de recuperarlos previniendo su pérdida?
- ¿Tienes el control total de los dispositivos móviles de tu compañía, bajo un modelo de administración de accesos centralizado en el que puedas definir uso de aplicaciones, consumo de datos y seguridad de la información?

Conoce el estado real de tus recursos informáticos
Realiza inventarios automáticos de hardware y software, detecta para cada dispositivo el software instalado licenciado y sin licencia, los costos de licencias y la información relacionada con los programas y sistemas operativos.
Detecta las licencias instaladas para cada dispositivo y controla el licenciamiento de software para tus equipos
Conoce los recursos de software adquiridos por tu organización, el valor y ubicación de los mismos, facilitando la gestión de compra, uso, control y actualización de estos activos.
Mantén actualizadas todas las estaciones de trabajo de tu organización sin interrumpir el trabajo de tus empleados
Previene ataques externos y riesgos de seguridad, manteniendo actualizadas todas las estaciones de trabajo de tu organización, con los últimos parches y actualizaciones liberadas por los fabricantes de soluciones.
Distribuye de forma centralizada la instalación de software y archivos en tu red corporativa
Programa la distribución e instalación automática del software y archivos requeridos por tu equipo remoto, de forma desatendida y sin interferir en la productividad de tus colaboradores.
Inventario de dispositivos móviles y gestión de aplicaciones
Conoce el estado real de tu red de dispositivos móviles con detalles actualizados de hardware del dispositivo, aplicaciones instaladas, estado, ubicación, características de red, fabricantes, sistemas operativos y ubicación que pueden ser consultados desde la consola de administración en cualquier momento.
Gestión y aplicación de políticas de comportamiento en tus dispositivos
El administrador de IT podrá enviar a los móviles la configuración inicial requerida para que puedan ser usados apropiadamente: acceso a redes wi-fi, correo electrónico del empleado, aplicaciones necesarias para el trabajo, restricciones para asegurar un buen uso del dispositivo, listados de aplicaciones requeridas /prohibidas, políticas de contraseña, etc.
Conjuntos de reglas de negocio + Voz y datos
Se pueden asignar conjuntos de reglas de negocio a los dispositivos para definir su comportamiento ante eventos relevantes, tales como la entrada o salida de zonas geográficas (geofencing), la desvinculación del móvil iniciada desde el dispositivo, la desvinculación realizada desde consola, el incumplimiento de políticas, detección de jailbreak, detección de rooteo, entre otros.
Separación segura de ambientes corporativo y personal
Administra de manera segura las aplicaciones e información corporativa que se comparte en los dispositivos que utilizan ambientes separados (Android for work) al interior de tu organización, a su vez que mantienes protegidos los datos y contenido personal de los propietarios del dispositivo.
Backup & Recovery
Ofrece a tu organización una poderosa protección multicapa contra el robo de datos y el acceso no autorizado a tus archivos respaldados a través de funcionalidades como cifrado en puntos finales, borrado remoto y la prevención en robo de datos.
Reduce el riesgo de migración de datos
El área de IT puede fácilmente ubicar y respaldar los datos críticos que se encuentran en ubicaciones no definidas en equipos de escritorio o portátiles, reduciendo el riesgo de no migrar toda la información crítica del negocio.
Protección de la data en los dispositivos móviles
Cifrado de los datos corporativos que se encuentran al interior del dispositivo, borrado remoto, bloqueo en modo seguro y geolocalización en tiempo real, a su vez que brindas acceso confiable a los documentos de la organización con diferentes niveles de control de acceso.
Backup de los archivos PST del correo de Microsoft
Soporte a archivos abiertos a través de la integración con Microsoft VSS permite realizar el backup de los archivos PST mientras que Microsoft Outlook está abierto.
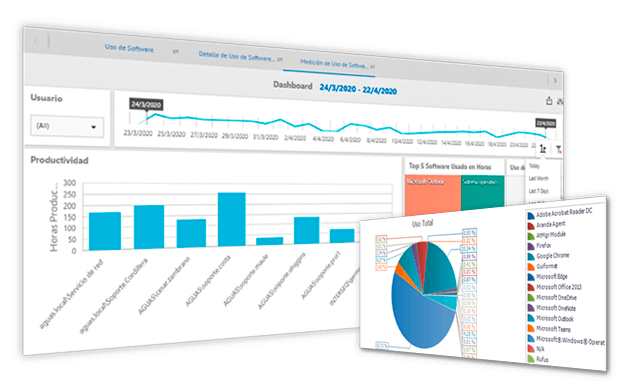
Define indicadores de productividad según el uso de las aplicaciones
Identifica los niveles de uso de las herramientas instaladas en cada estación de trabajo en un tiempo determinado (días, semanas, meses o períodos críticos).
Control y administración remota
Ejecuta actividades de monitoreo y administración sobre cada estación de trabajo, efectuando todas las tareas de configuración de forma remota, como apagar o reiniciar la estación de trabajo, borrar un archivo, entre otras.
Supervisa acciones no autorizadas que hagan los usuarios remotos en los dispositivos
Detecta acciones como instalaciones de software, manipulación de Hardware, bajada de servicios, creación de recursos compartidos, instalación de adaptadores virtuales VPN, e ingreso de usuarios no autorizados en los equipos, entre otros.
Analiza el desempeño de tus colaboradores
Accede a reportes del histórico o bitácora del uso de todo el software estableciendo una medición por categorías: fecha, período, usuario, archivo, licencia o aplicación indistintamente la marca y/o fabricantes de software.
